Security remains a consistent priority for cloud providers to ensure that customers are always protected, data is secure and applications are safe. Users of Google Kubernetes Engine (GKE) are provided with ways to maintain the integrity of the compute instances that applications are running on top of. One functionality that is now enabled by default for GKE users is Shielded GKE Nodes, which prevents exploitation of any vulnerabilities within your Kubernetes pods and keeps attackers from being able to impersonate nodes in your cluster.
For our Ocean customers who use GKE, Spot has rolled out support of Shielded Nodes to ensure that any node provisioned by Ocean is protected under this functionality.
How does it work?
In version 1.18 of GKE, newly created nodes have the configuration for shielded nodes by default. With this configuration, it’s required that the Certificate Signing Request (CSR) of the new nodes is approved. For nodes that are part of a node pool, this approval is taken care of by GKE. When Ocean launches a new virtual machine, the Ocean controller (version 1.0.73 or higher) will take care of validating the added node and approving its CSR.
Ocean users will get this new function right out of the box and can spin up new node and node pools knowing that their pods are secure. For existing node pools, users will need to recreate the launch specifications so Ocean can import these new configurations.
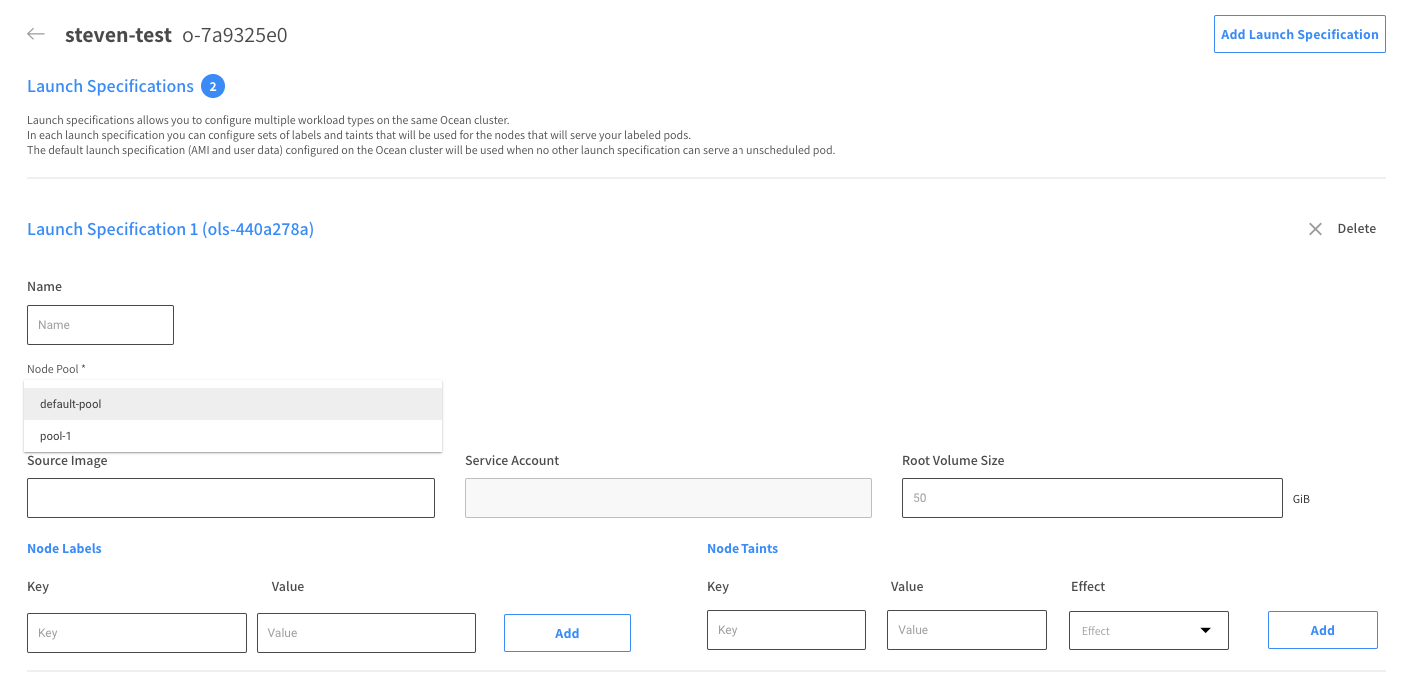
Follow these steps to recreate a launch specifications and use the Shielded Node configuration in any new virtual machine Ocean launches:
- Open the Ocean console and navigate to the launch specifications view
- Click “add launch spec” and choose the relevant nodepool to associate the new configuration with
- Once the new launch spec is created, remove the old launch spec
For more details about Ocean for GKE, please refer to the relevant documentation.

