Whether you are new to AWS or have been to every re:Invent since 2012 you may have questions about cloud security and how it impacts your valuable technology and data. In particular, you might be wondering where AWS’s security responsibilities end and where yours begin? Which parts of the cloud can you rely on Amazon’s security team and technology to keep safe and which parts must you take care of?
To better understand these issues, let’s take a look at the AWS Shared Security Model.
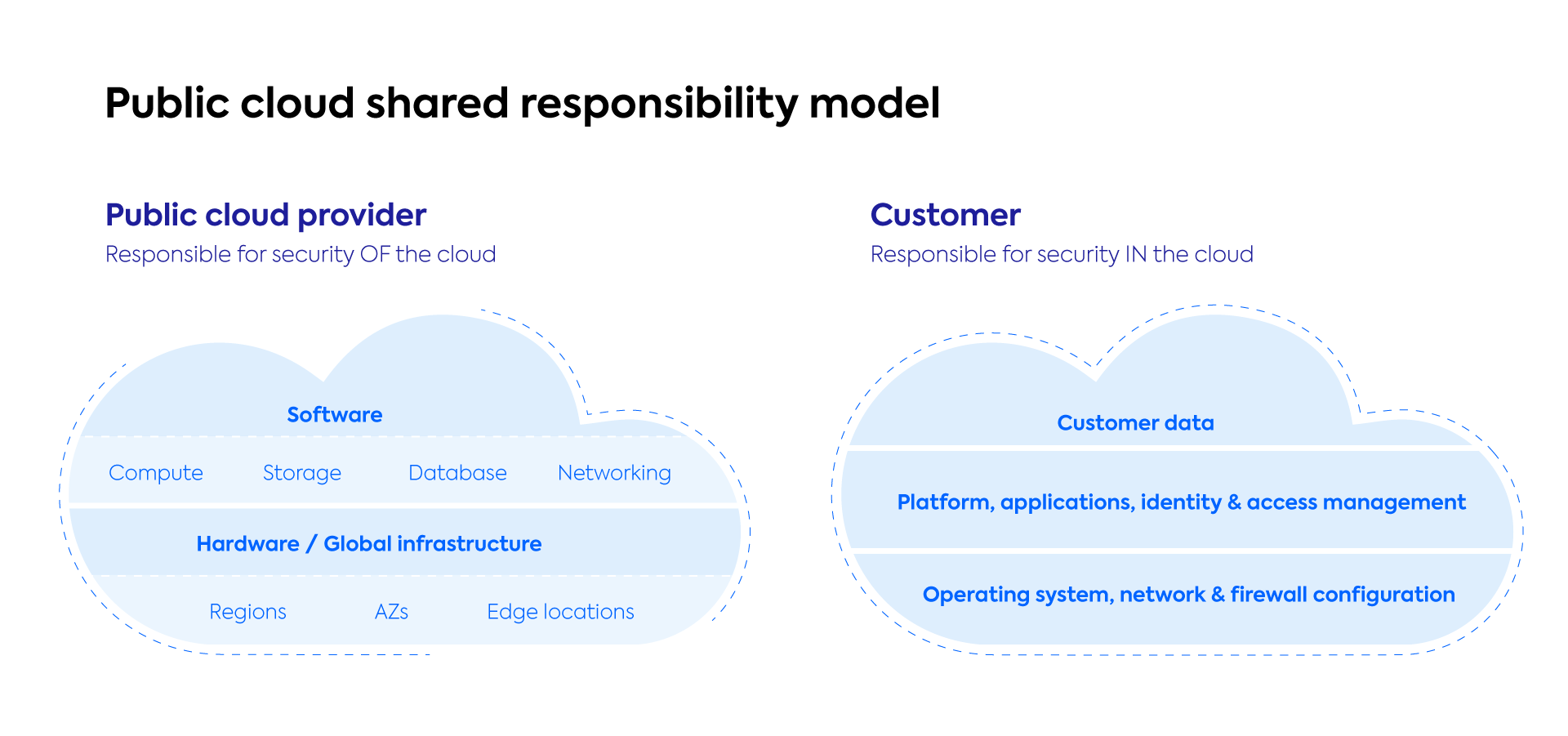
What is the AWS Shared Security Model?
When it comes to cloud security and compliance, the AWS Shared Security Model takes a “divide and conquer” approach. Responsibility for components such as the host OS, the virtualization layer, physical hardware, infrastructure and data center facilities all fall under AWS’s purview. On the customer side, you must take care of things like guest OS, any running applications and workloads, data encryption, firewall configuration, and similar.
This model not only lightens your day-to-day security management load, it also provides a clear delineation of liability in case of any security breaches. But most importantly in practical terms, the AWS Shared Security Model provides a template of what you need to be aware of and protect on your own while informing you of what AWS promises to keep secure. This allows you to take an educated approach to how much of your data you want to place in the cloud, how much control you wish to share with AWS and where appropriate measures must be taken by you to protect your business from any potential security threats.
AWS codifies their shared model into what they refer to as “security Of the cloud” and “security IN the cloud”. Let’s take a closer look at each to understand AWS’s and the customers’ place in securing the entire cloud.
Security OF the Cloud
AWS focuses exclusively on the security of their infrastructure, and as they describe it, this includes “the hardware, software, networking, and facilities that run all AWS Cloud services.”
Because AWS takes security so seriously, and because they are unequivocally the leader in all things public cloud, this means that the cloud itself is well protected — a great first step towards true data security in our all-too-often insecure world.
As part of this, AWS is responsible for all global infrastructure which includes regions, availability zones, and edge locations, as well as the software and hardware of all storage, database, networking services.
On the other hand, according to Gartner, 99% of all cloud security failures (through 2025) will be to the customer’s fault. This leads us directly to “security IN the cloud”.
Security IN the Cloud
Think of AWS as a locker in a gym. It’s convenient, sturdy, and able to hold all of your valuable, personal items such as your wallet or keys—but it is still your responsibility to lock up the locker to ensure these items are fully secure once when inside.
Similarly, when it comes to cloud security AWS handles everything below the hypervisor layer—all the hardware, software, networking, and physical facilities that comprise the public cloud structure where you can put all your valuable business workloads, data and operations. But as the customer, you still need to handle everything above the hypervisor layer such as identity, policies, configuration, encryption and the like, to keep everything safe once inside the cloud.
This is why understanding the AWS Shared Security Model is so important. Without a full and comprehensive understanding of what this means, you could unknowingly leave your data and resources vulnerable within the cloud.
Let’s break down all main components above the hypervisor level that you as a customer need to secure:
- Your (customer) data
- Platforms
- Identity and access control
- Applications
- Encryption
- OS
- Network
- Firewall configuration.
This means that all of the data you choose to be responsible for, all the apps you use and passwords you save, the security parameters you put in place, and your very identity are your responsibility.
AWS relies on you to put the correct security parameters in place inside the cloud. Essentially, cloud users are responsible for configuring security groups (firewall), implementing access controls accordingly, enabling CloudTrail, enforcing data-loss prevention policies as well as detecting and identifying threats so as to remove them accordingly.
Getting started with security IN the cloud
With hacking becoming more prevalent in our increasingly digital society, the need for accountability and a security framework like the AWS Shared Security Model is more necessary than ever before. However, as a cloud customer, just managing “security IN the cloud” can still be extremely complex. With so many employees having access to the cloud accounts, simple human error such as misconfiguration and the like, can have disastrous outcomes. In our next post we will discuss the top 10 security threats that you need to be aware of. Until then, safe clouding!