Earlier this year, a new user management system was announced, designed to give Spot’s users more granular control on their Spot resources at both the organization and account levels.
As we got very good feedback from customers, we are now happy to announce a new feature in the user management system called Custom Policy Conditions.
The condition feature allows users with policy modification access to create conditions within the policy. It also adds another granular level for the policy effect, which should take place only if the condition requirements are met.
The condition building blocks are:
- condition operators, which contains condition keys:
- resource retrieval
- resource attribute
- condition values (attribute value) that should match keys and values received for the given resource in the request
In this way, one can get allow / deny access to a specific resource only if the condition inside the policy matches the requested data (e.g., resource name, resource inner configuration, etc.).
Technical explanation for the condition configuration
Let’s see a few examples in action. Given an Elastigroup resource:
{
"group": {
"name": "eg-example",
"compute": {
"launchSpecification": {
"tags": [
{
"tagKey": "DeveloperEmail",
"tagValue": "example@mail.com"
}
]
}
}
}
}
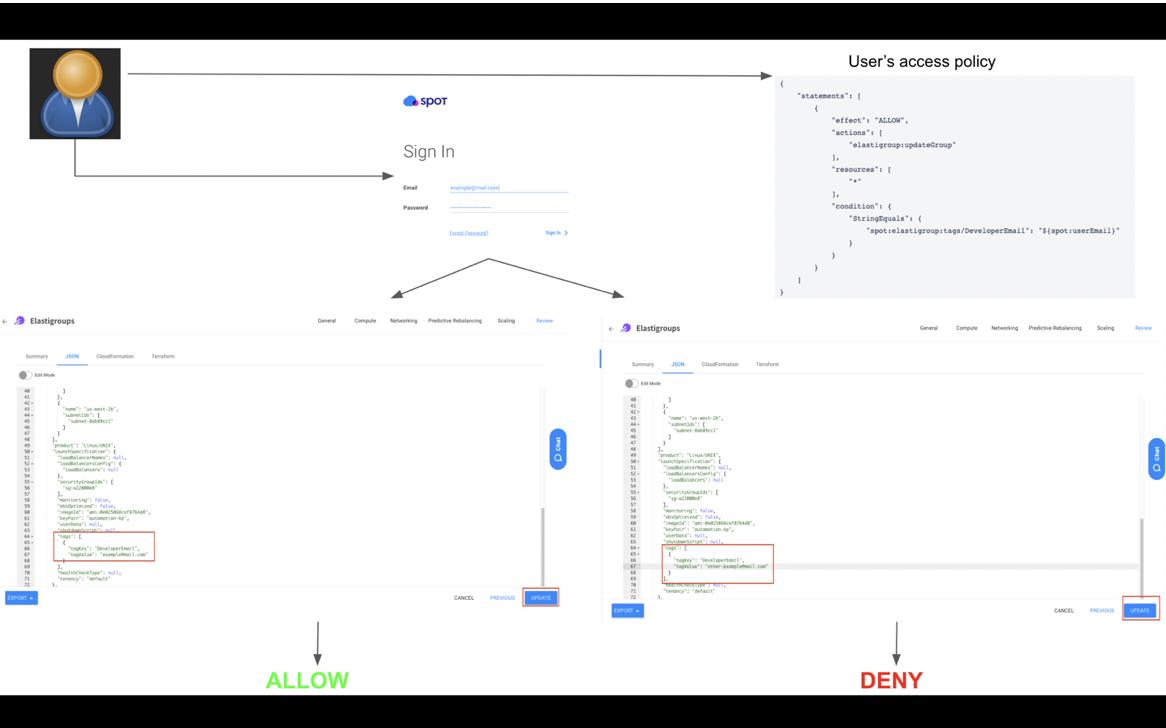
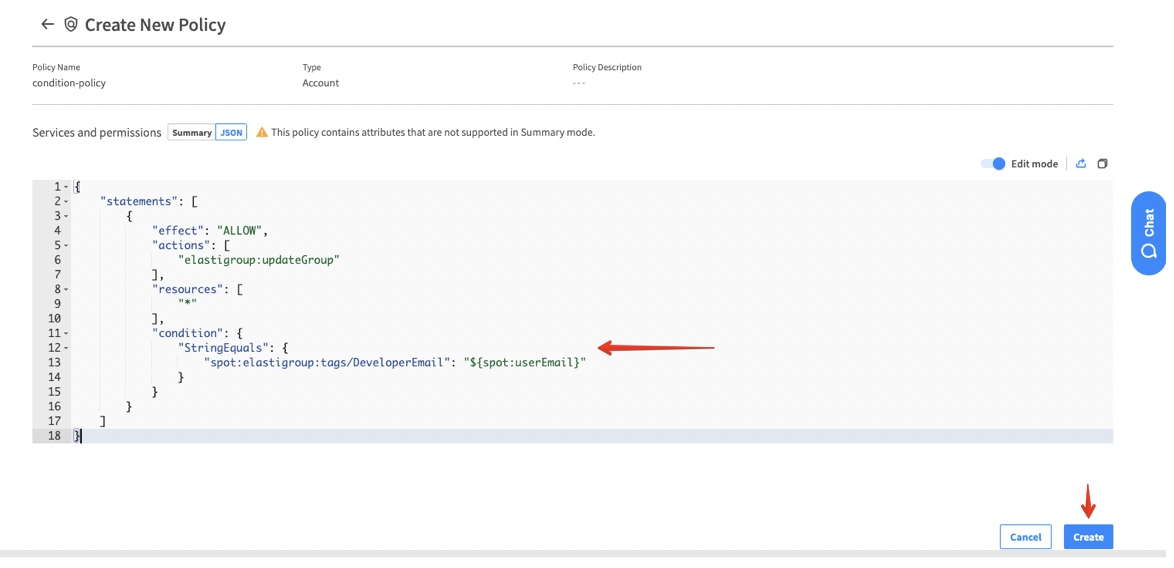
The following policy will allow update actions for users with the email example@mail.com as specified in the tag with key DeveloperEmail from the Elastigroup above.
{
"statements": [
{
"effect": "ALLOW",
"actions": [
"elastigroup:updateGroup"
],
"resources": [
"*"
],
"condition": {
"StringEquals": {
"spot:elastigroup:tags/DeveloperEmail": "${spot:userEmail}"
}
}
}
]
}
In the case above, the attribute (tag with the key of DeveloperEmail) exists in the Elastigroup and matches the resource attribute in the policy (“spot:elastigroup:tags/DeveloperEmail”). Therefore, the user whose email is defined as example@mail.com can make the actions that were defined in the policy (i.e., update Elastigroup).
Notice that the attribute value is defined as a variable ${spot:userEmail} and not a constant value. (See more details in the condition resource value section below.)
Caption: Permission configuration workflow
Enabling Ocean-related operations
{
"statements": [
{
"effect": "ALLOW",
"actions": [
"ocean:*"
],
"resources": [
"*"
],
"condition": {
"StringEqualsIgnoreCase": {
"spot:ocean:name": ["ocean-example-1", "ocean-example-2"]
}
}
}
]
}
In the case above, the user mapped to this policy will be able to perform all Ocean-related operations on Ocean clusters with a name that contains ocean-example-1 or ocean-example-2.
Understanding condition blocks
In this section, we will review different parts of the condition blocks and list all the supported configurations in each part.
Condition consists of four parts:
- Condition operator
- Resource retrieval
- Resource attribute
- Attribute value
1. Condition operator
The operator field defines the logic to be checked between the operands condition attribute value and actual retrieved value.
Note: A missing attribute in the retrieved attribute value will be considered a mismatch. Therefore, the condition will return false and will not enforce the policy effect.
Following are the available operators:
- StringEquals — Compares two strings and returns true if equals, otherwise returns false.
- StringNotEquals — Compares two strings and returns false if equals, otherwise returns true.
- StringContains — Compares two strings and returns true if the first string contains the second, otherwise returns false.
- StringEqualsIgnoreCase — Compares two strings and returns true if the strings are the same length and corresponding characters in the two strings are equal, ignoring case.
2. Resource retrieval
Resource retrieval is responsible for the definition of which resource should be tested with the condition operator. It specifies which resources should be retrieved for testing.
This consists of two mandatory parts that are separated by the character:
- Spot prefix — spot
- Resource name — A single resource out of the available resources: managedInstance, elastigroup, ocean.
3. Resource attribute
A resource attribute is a single attribute out of the available attributes from the resource configuration.
Supported attributes are: name, tags.
This part may contain inner definition (optional) resource attribute key. It should be separated by the character / followed by some key that exists inside the attribute.
For example, the resource attribute is tags, and we are only interested in the tag with the key DeveloperEmail.
Examples for a full resource retrieval definition:
- “spot:ocean:name”
- “spot:elastigroup:tags/Email”
4. Attribute value
Specifying the value should be test against the retrieved value within the retrieved resource.
The attribute value can be as follows:
- Single string
- Single variable
- Supported variables: ${spot:userEmail}
- An array of values: Can be composed from each combination of the two types above. See the usage example below.
Notes
Resource retrieval
Currently, this feature supports AWS resources only.
Multiple condition operators
In case the condition configuration contains more than one condition operator, the operators will be tested using a logical AND. This means that in order to enforce the policy effect, all operators should return true.
Multiple attribute values
Allowing the condition to have multiple attribute values in the same field is possible (e.g., spot:elastigroup:name”: [“elastigroup-1″,”elastigroup-2”]). In that case, the logical OR will take place in the test. Therefore, the Elastigroup resource name should match either elastigroup-1 OR elastigroup-2.
Multiple resources
A condition is defined using a single operator and a single resource. However, you may want to define a condition for multiple resources, such as allowing access for all resources with a name that equals My_Resource, or for both an Elastigroup resource and an Ocean resource. In those cases, you will need to define a separate policy for each resource and map each policy to the relevant user.
Creating policies in the Spot Console
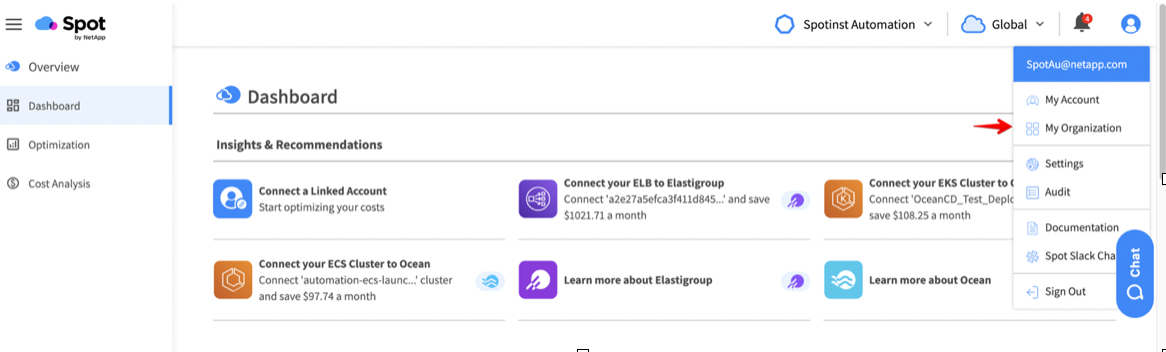
Use the following steps to create an access policy using the Spot Console.
1. Under your User icon in the upper righthand corner, select My Organization from the dropdown menu:
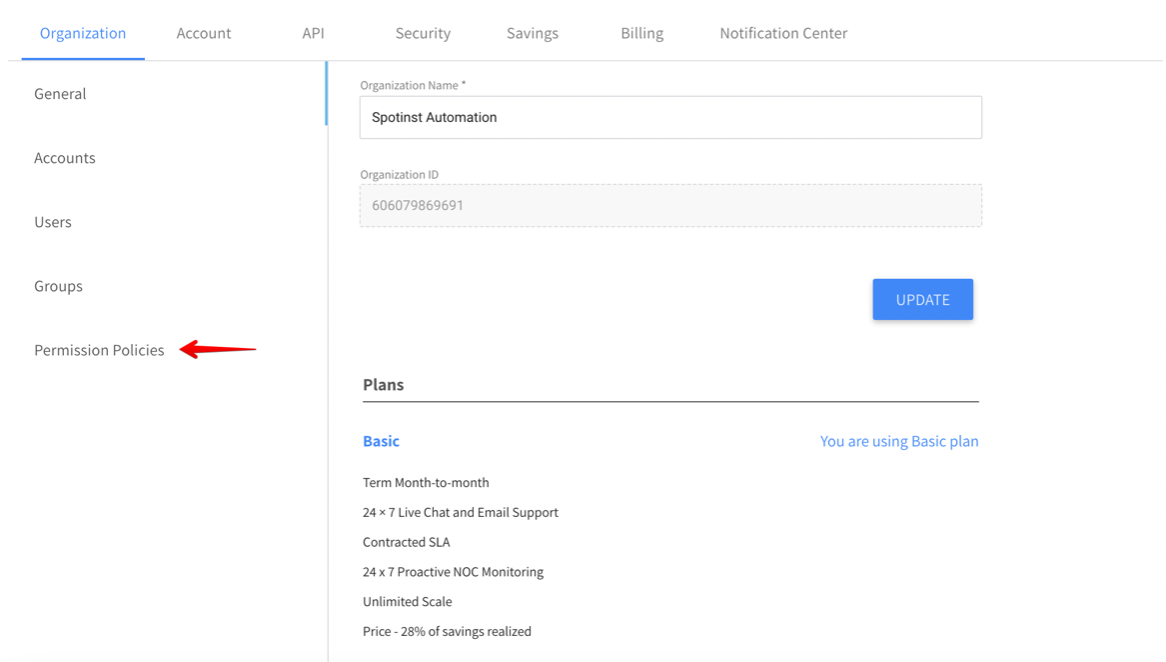
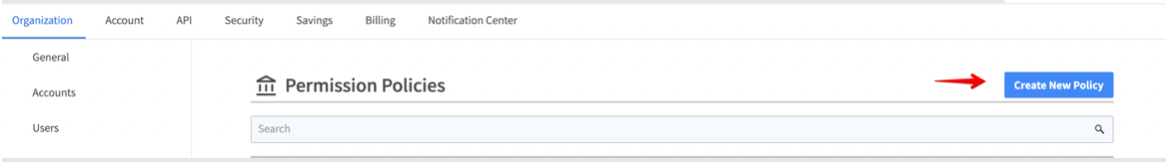
2. From the lefthand menu, select Permission Policies.
3. On the Permission Policies screen, click the button that says Create New Policy.
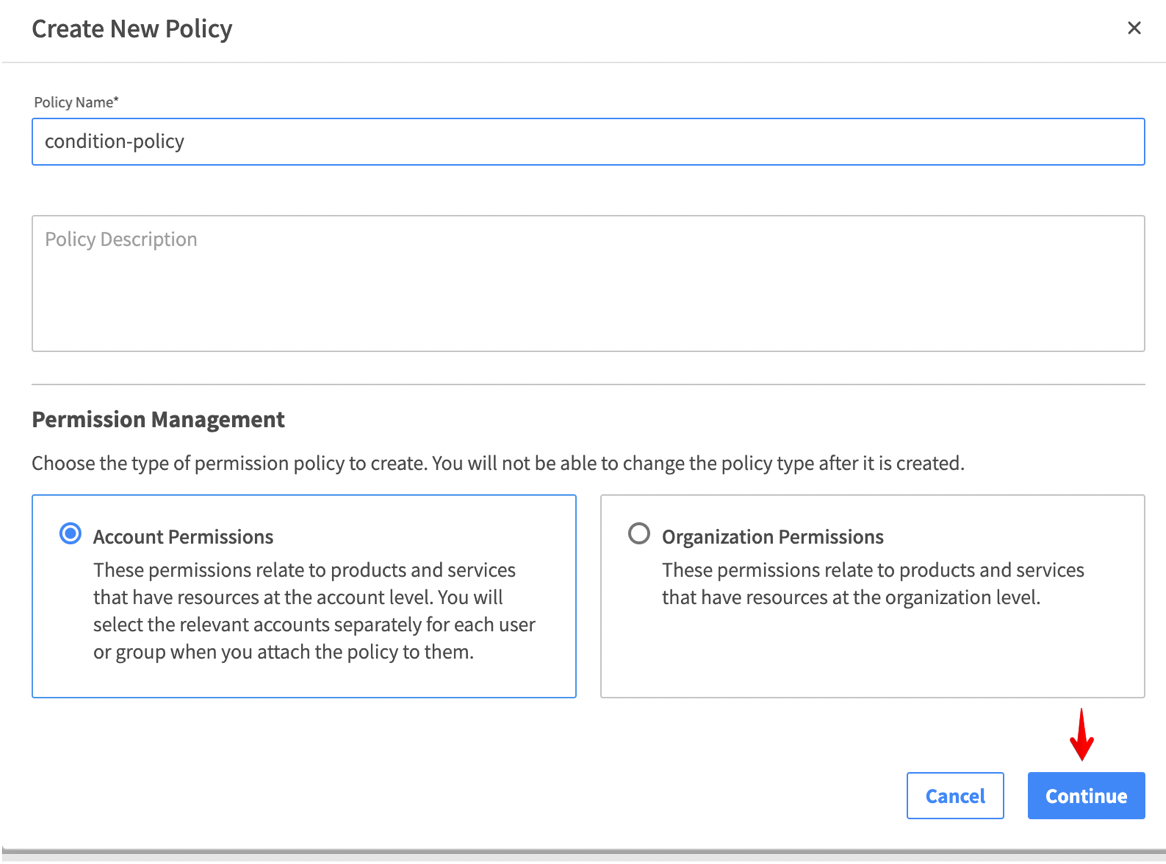
4. Next, choose the Policy Name and set the policy scope in the Permission Management settings. When you’re done, click Continue.
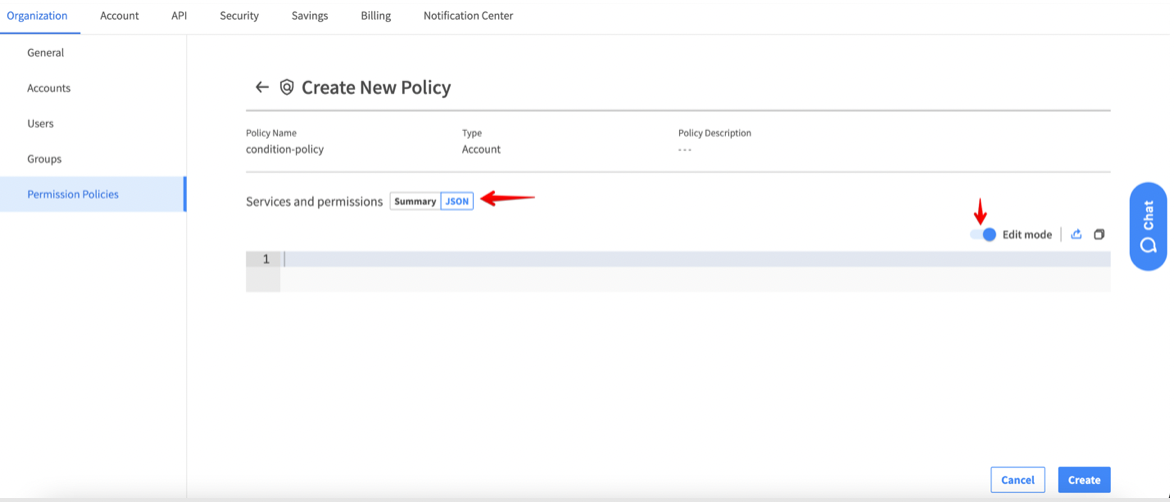
5. On the next screen, go to the JSON tab and toggle Edit mode to “on.”
6. In the text field, add the policy JSON configuration, including the condition block. When you’re done, make sure to click the Create button below, and your policy is set.
What’s next?
Currently, only Spot’s AWS resources are supported. We will soon support Azure resources as well.
To read more about assigning policies to users or user groups, please visit our documentation page here.