What Is Docker Security?
Docker is a popular container engine that packages applications and their dependencies into lightweight units that can run anywhere. Docker security involves safeguarding containerized applications and infrastructure against unauthorized access and malicious threats. It includes securing the containers, the container runtime, the host OS, and the software supply chain from vulnerabilities.
Effective Docker security integrates practices and tools throughout the container lifecycle, from development to deployment, ensuring the integrity and confidentiality of containerized applications.
Securing Docker containers is critical due to the increased use of the platform in mission-critical environments and the sensitive workloads and data stored within containers. Without proper security measures, containers can become entry points for attackers. Adopting Docker security best practices helps maintain the isolation between containers, protect sensitive data, and prevent unauthorized access, protecting both organizations and application users.
This is part of a series of articles about container security.
Related content: Read our guide to container monitoring.
Learn more in our detailed guide to container security best practices.
In this article:
What Are the Main Security Risks in Docker Containers?
Here are some of the primary security issues you might encounter when running Docker containers:
Unrestricted Traffic and Unsafe Communication
Unrestricted traffic between containers can expose sensitive data and systems to unauthorized entities. Without proper network controls, attackers can eavesdrop on communications, leading to data breaches. Ensuring secure communication through encryption and network policies is essential to protect data in transit.
Implementing network segmentation and firewall rules helps limit the traffic flow between containers, minimizing the risk of lateral movement by attackers. Adopting these measures ensures that even if one container is compromised, the impact on other containers and the host system is contained.
Vulnerable and Malicious Container Images
Container images with known vulnerabilities or embedded malicious code pose significant security risks. Attackers can exploit these vulnerabilities to gain unauthorized access or execute arbitrary code within containers. It’s crucial to scan container images for vulnerabilities and ensure they come from trusted sources.
Proactively updating container images and using only verified images from reputable registries can mitigate these risks. Establishing policies for image validation and continuous monitoring for new vulnerabilities ensures containers are secure against known threats.
Unrestricted Access
Granting excessive privileges or unrestricted access to containers can lead to security breaches. Containers should operate with the least privilege necessary, limiting the potential impact in case of compromise. Implementing access controls and user authentication mechanisms is essential to safeguard containers against unauthorized access.
Regularly reviewing permissions and implementing role-based access controls (RBAC) ensure only authorized users have the necessary access to containers. This minimizes the attack surface and enhances container security.
Host Kernel Vulnerabilities
Containers share the host kernel, making vulnerabilities within the kernel a significant concern. Exploiting these vulnerabilities can compromise the host and all containers running on it. Keeping the host system and kernel updated is vital for security.
Kernel vulnerabilities often target isolation technologies such as namespaces and cgroups. Employing additional kernel security mechanisms, such as SELinux or AppArmor, further strengthens the security posture against kernel-level exploits.
Breaking Out of Containers
The ability of attackers to break out of containers and gain access to the host system or other containers is a critical security risk. This can occur through misconfigurations or exploiting vulnerabilities. Ensuring proper isolation and implementing security measures are crucial to prevent container escape.
Regularly auditing container configurations and employing security tools to detect and mitigate potential escape vulnerabilities enhances container security. Keeping software up to date and adhering to security best practices reduces the risk of container breakout.
Docker Security Best Practices with Examples
1. Keep Host and Docker Up to Date
Regular updates to the Docker engine and the host operating system are fundamental for security. These updates often include patches for vulnerabilities that could be exploited by attackers. Employing automated tools for patch management ensures timely application of security updates.
Besides updating, monitoring vulnerability databases and security bulletins provides insights into potential threats. This can help you defend against exploits targeting known vulnerabilities in the Docker ecosystem and host environment.
Code example
Here is how to update Docker and the underlying host operating system on Ubuntu. You will first need to log into the container using the docker exec command.
# Update Docker Engine on Ubuntu
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io
# Update the host system of the container(s)
sudo apt-get update
sudo apt-get upgrade -y2. Run Docker in Rootless Mode
Running Docker in rootless mode enhances security by limiting the potential impact of a compromised container. In this mode, the Docker daemon and containers run without root privileges, reducing the risk of privilege escalation. This approach minimizes the attack surface, making it harder for attackers to gain elevated access through Docker containers.
Code example
The following code snippets show how to install and run Docker in rootless mode.
First, make sure you have uidmap package installed:
sudo apt-get install -y uidmapYou are now ready to install Docker in rootless mode:
# Install rootless Docker
curl -fsSL https://get.docker.com/rootless | sh
# Set up the environment for rootless Docker
export PATH=/usr/bin:$PATH
export DOCKER_HOST=unix:///run/user/$(id -u)/docker.sock
# Verify rootless Docker is running
docker info3. Segregate Container Networks
Network segregation limits the potential for unauthorized access between containers. Implementing network policies and using separate networks for different applications or services enhances security by controlling communication flows. This strategy prevents attackers from moving laterally across containers and accessing sensitive data.
Code example
The following example shows how to create separate networks for two different components, an application and a database, both hosted in Docker containers:
# Create two separate Docker networks
docker network create app_network
docker network create db_network
# Run containers in separate networks
docker run -d --name app_container --network app_network my_app_image
docker run -d --name db_container --network db_network my_db_imageThe output should look like this:
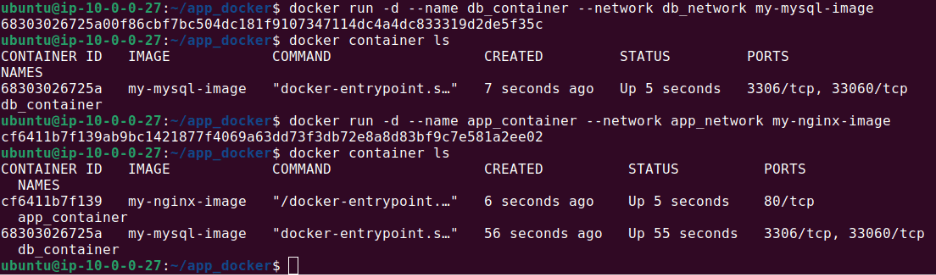
4. Use Docker Content Trust to Verify Image Authenticity
Docker Content Trust provides a mechanism for verifying the authenticity and integrity of container images. By signing images, authors can assure users of their origin and that they haven’t been tampered with. Enabling Docker Content Trust helps in validating the authenticity of images before deployment. This mitigates the risk of deploying malicious or compromised images.
Code example
Here is how to use Docker Content Trust when pulling an image from a repository:
# Enable Docker Content Trust
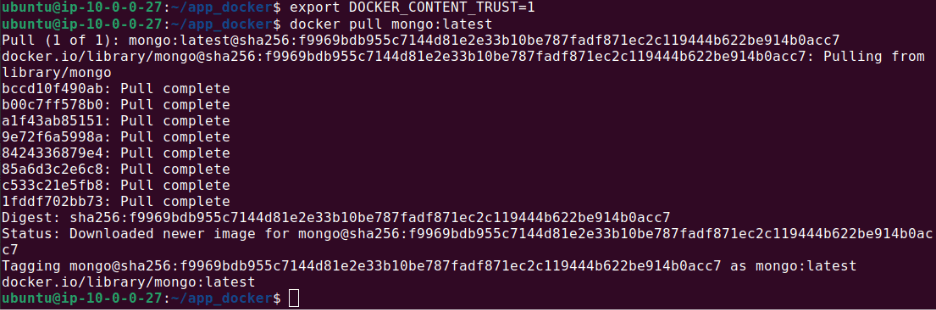
export DOCKER_CONTENT_TRUST=1
# Pull an image with Docker Content Trust enabled
docker pull <image_name>:<tag>The output should look like this:
5. Lint Your Dockerfiles to Detect Unsafe Misconfigurations
Using linters to analyze Dockerfiles can detect potential misconfigurations and security issues. Linters highlight practices that may compromise security, such as using deprecated features or insecure base images.
Regularly linting Dockerfiles as part of the development process ensures adherence to best practices and enhances security. Incorporating linting into continuous integration and delivery pipelines automates the detection of issues, allowing for prompt remediation.
Code example
# Install Hadolint, a Dockerfile linter
sudo wget -O /bin/hadolint
https://github.com/hadolint/hadolint/releases/download/
v1.17.6/hadolint-Linux-x86_64
sudo chmod +x /bin/hadolint
# Lint a Dockerfile
hadolint Dockerfile6. Use Fixed Tags for Immutability
Using fixed tags for container images ensures immutability, preventing unintended updates or replacements. Fixed tags reference specific versions of images, unlike mutable tags like ‘latest’ which can change over time. This practice guarantees that the version of the image deployed is the version intended, reducing the risk of deploying images with vulnerabilities.
Adopting fixed tags enhances both security and reliability. It ensures consistent environments across development, testing, and production, minimizing the chances of vulnerabilities introduced through changes in images.
Code example
This command demonstrates the use of a fixed tag when pulling an image:
# Use a fixed tag for pulling an image
docker pull nginx:1.17.1Securing Your Containers with Spot Security
Designed for the cloud, Spot Security conducts agentless, real-time risk assessments to identify the most critical misconfigurations and vulnerabilities, based on the potential attack surface and cloud asset relationships.
With Spot Security, you can:
- Gain a holistic view of your cloud environment using risk impact maps to uncover even minor security gaps that can put your organization’s crown jewels at risk.
- Prioritize actionable insights with a single dashboard view based on the attack surface, risk severity and network exposure.
- Create groups of business-critical assets and track their security posture, access, permissions, and compliance status in a single view.
- Save time and effort by automating the remediation workflows with ready-to-use Python and CLI code.
Learn more about securing your cloud with Spot Security.
