Repetition is super helpful when learning something new. But eventually we get tired of repetitive tasks, errors start creeping in and the tedium saps us of the creative energy we need to innovate and problem-solve. This is why here at Spot we love AWS CloudFormation. It decreases errors, frees teams to focus on their core tasks and when used with our products, helps to dramatically optimize cloud infrastructure cost and utilization.
Today we are excited to share about our latest CloudFormation integration, with our flagship product Elastigroup now included in the CloudFormation Public Registry. But first, a bit about CloudFormation for those who are unfamiliar.
IAC or Infrastructure as Code
AWS CloudFormation is an infrastructure automation tool that provisions cloud computing resources. By creating a stack template, you can be confident your AWS cloud resources are built in a consistent manner. No more wondering if you, or a teammate, missed a step or forgot a checklist item.
CloudFormation stack templates can be stored in version control. You can keep your template updated as changes are made to your infrastructure. This provides your team with the ability to recreate your cloud infrastructure accurately anytime needed. No more redeploying, and then having to scramble to track down and reapply a bunch of post-deployment changes.
The next level of Spot integration with CloudFormation
Over the years, Spot has enjoyed increasingly tighter levels of integration with AWS CloudFormation. We’ve gone from needing a Lambda function (which after receiving instructions from a CFN stack would call the Spot API to take the necessary actions on our resources) to joining AWS’s CloudFormation Registry as a private, 3rd party resource all the way to today where we are now part of CloudFormation’s Public extensions registry.
This latest integration brings two key benefits:
- Installation is simplified – it is no longer necessary to manually add Spot’s custom private registry/resource type.
- Maintenance and version update overhead is greatly reduced so customers receive the latest Spot feature without delay.
This means that you can easily and instantly use CloudFormation to provision cloud infrastructure thru Spot’s Elastigroup helping you save even more time and of course, optimizing your cloud spend and utilization.
Keeping the Spot::Elastigroup::Group resource type up to date has also been streamlined. Automatic updates for minor and patch releases can be enabled. When a major release happens, you’ll be able to choose to activate the upgrade from right inside the UI.
Getting started
The new public resource can be activated from the AWS console, with just a couple of preparatory steps:
- Navigate to CloudFormation under your AWS account and verify that you are in the correct AWS region.
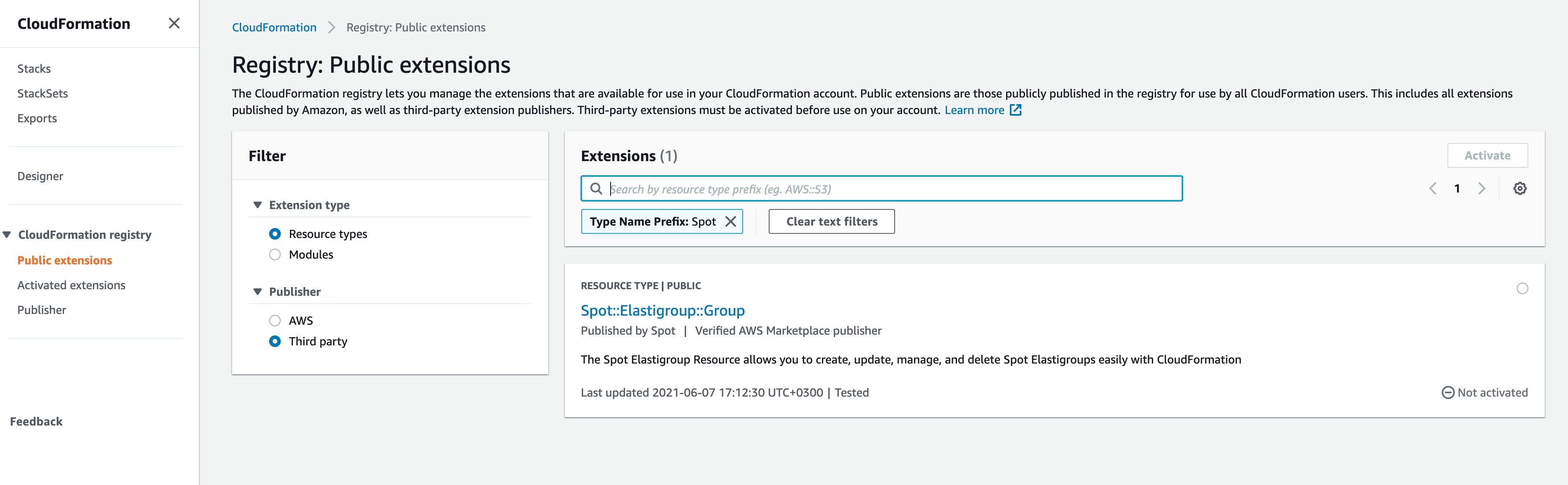
- From the left sidebar, under CloudFormation registry, choose Public extensions.
In the Filter menu under Publisher, choose Third party, and search for “Spot” to find all our custom public resources. In this example we’re looking for Spot::Elastigroup::Group.
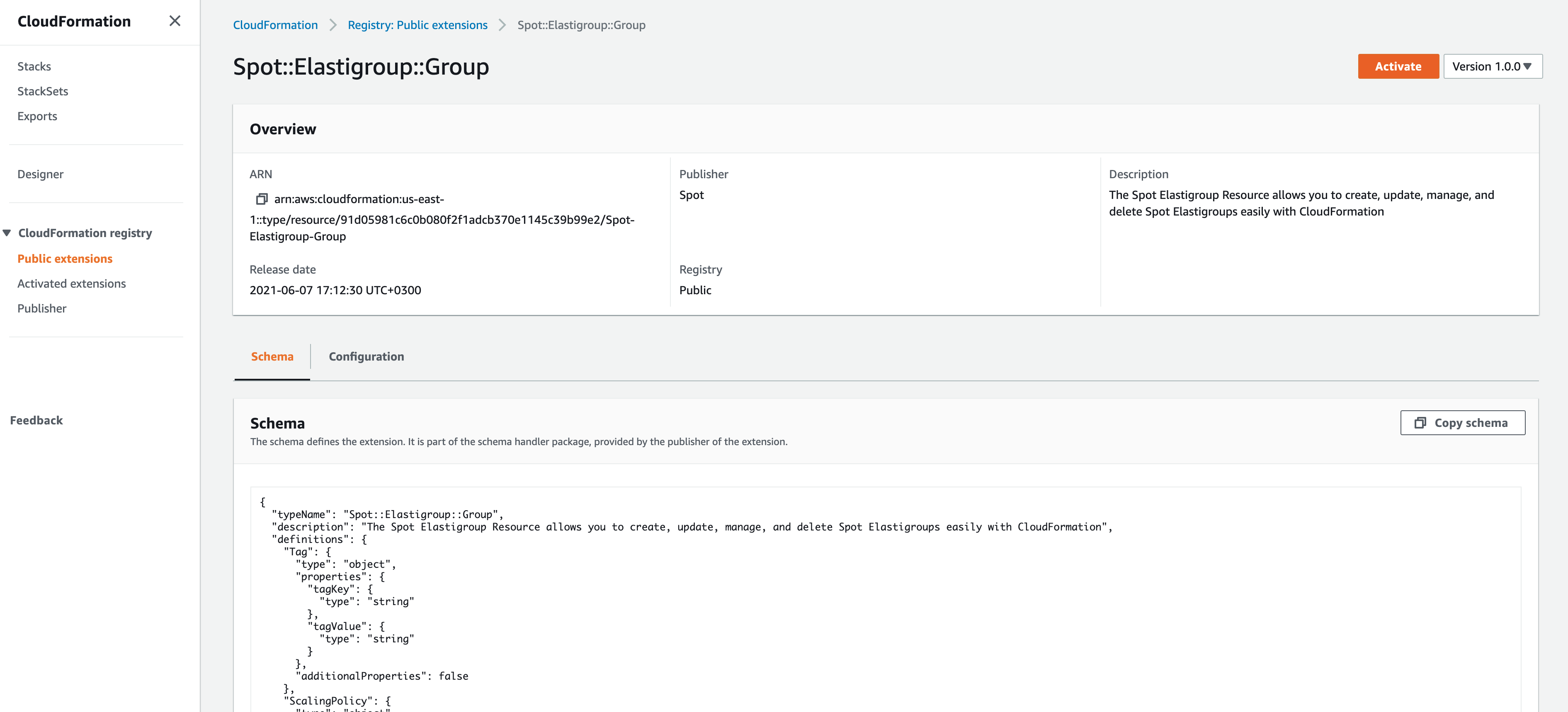
Click on the Spot::Elastigroup::Group link and choose Activate in the upper right corner of the overview screen.
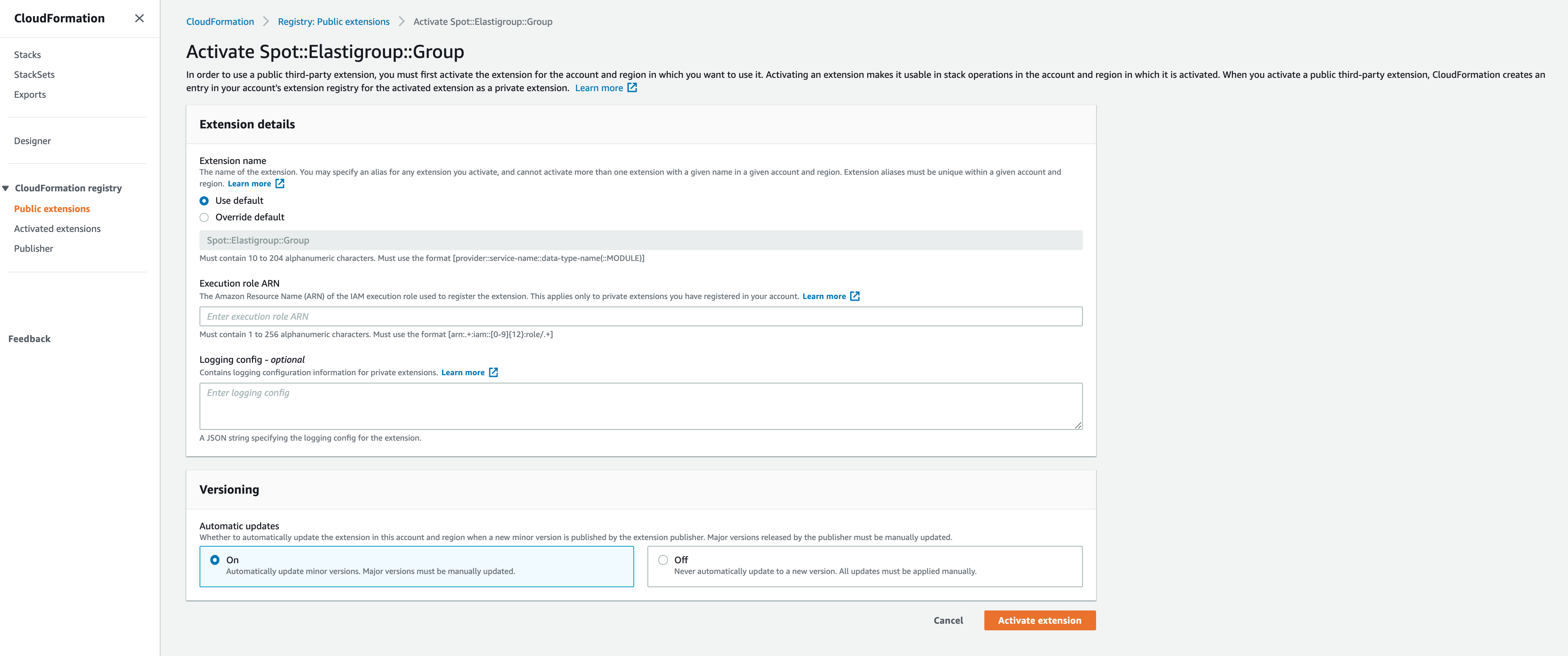
You’ll be prompted for a few configuration items.
- The first is the option to override the default name.
- The second is a required “Execution role ARN” for this public extension. This role must have a trust relationship established with CloudFormation, but does not need permissions to access resources in your account. Once this ARN is created, it can be reused to activate the public resource type in additional regions.
- The remaining configuration items for logging and versioning can be left at their default settings. You’ll be able to modify them after activation if the need arises.
- To create the required “Execution role ARN” navigate to “IAM” under your AWS account and click on “Roles”. You may want to do this in another tab, so you can keep this one open.
- Create a Role with “AWS service” as the trusted entity and select “CloudFormation” as the use-case.
- When choosing which policies to attach the newly created role, select “AWSDenyAll” (This is because our custom public type does not need to access any resources in your AWS account).
- After the role has been created, verify that its trust-relationship with CloudFormation service exactly matches the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "resources.cloudformation.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
- Copy and paste the newly created role’s ARN into the Public extension configuration screen and click “Activate”.
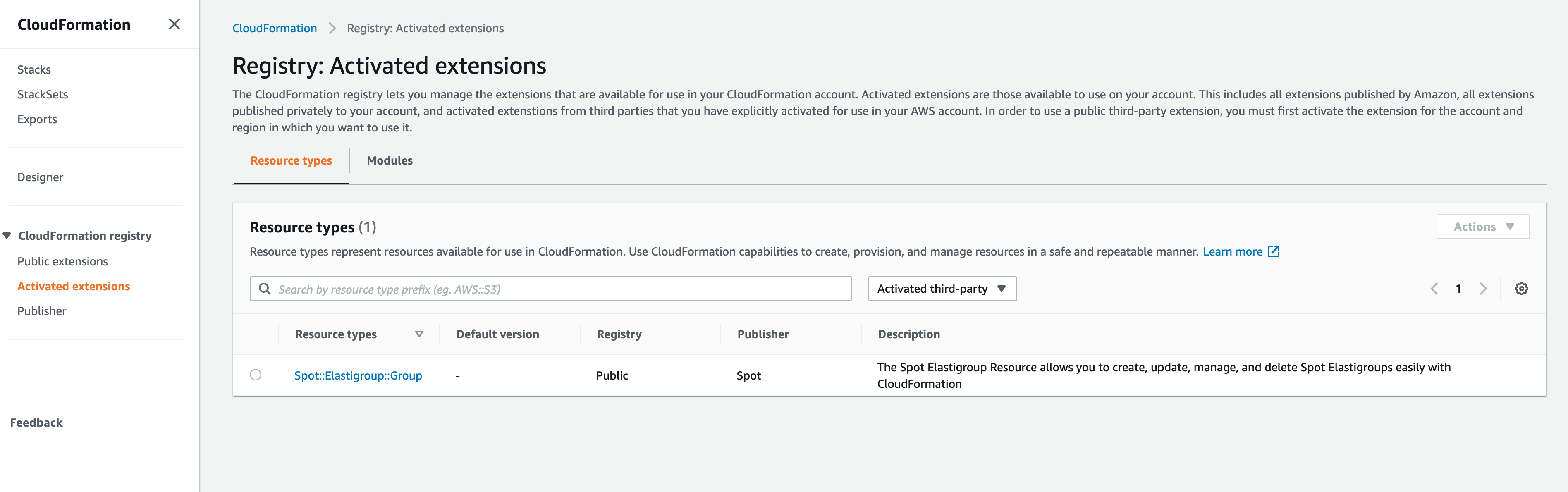
- You will now see “Spot::Elastigroup::Group” under “Activated extensions.” Your CloudFormation stacks can now refer to it as a native resource type!
- If you or your organization use multiple AWS regions, simply repeat the activation process in each specific region. Remember that you can use the same Execution role ARN across all regions.
Post-activation screenshot:
Here is an example CloudFormation template to bring up a new Elastigroup.
Note: Substitute values where relevant.
AWSTemplateFormatVersion: '2010-09-09'
Resources:
SpotinstElastigroup:
Type: Spot::Elastigroup::Group
Properties:
credentials:
accessToken: XXX
accountId: XXX
group:
name: myCfnGroup
description: my CFN Elastigroup description
strategy:
risk: 100
availabilityVsCost: balanced
drainingTimeout: 120
fallbackToOd: true
revertToSpot:
performAt: always
capacity:
target: 0
minimum: 0
maximum: 0
unit: instance
scaling: {}
compute:
instanceTypes:
onDemand: t2.micro
spot:
- t2.micro
availabilityZones:
- name: us-east-2a
subnetIds:
- subnet-XXX
- name: us-east-2b
subnetIds:
- subnet-XXX
- name: us-east-2c
subnetIds:
- subnet-XXX
product: Linux/UNIX
launchSpecification:
securityGroupIds:
- sg-XXX
monitoring: false
ebsOptimized: false
imageId: ami-XXX
tenancy: default
scheduling: {}
thirdPartiesIntegration: {}
In summary, Spot’s inclusion in the AWS Cloudformation Public Registry means that our customers have practically zero overhead when using CloudFormation to provision cloud infrastructure thru Spot’s Elastigroup. This makes it easy to fully control your deployments while dramatically reducing cloud costs.