The cloud not only ushered in a different way of developing and deploying software, but it also introduced a fundamentally different security reality, presenting new challenges to teams responsible for keeping environments secure. Designed to be dynamic, cloud environments can be in a near-constant state of change, with infrastructure resources spun up and down multiple times a day to support cloud applications. With each event, the building blocks of cloud infrastructure have to remain secure, but doing so is a big challenge for many organizations. In fact, Gartner estimates that 99% of cloud attacks are due to misconfiguration and mismanaging cloud infrastructure.
To help our customers successfully manage this critical component of their cloud operations, Spot is excited to announce Spot Security, a new product designed to keep cloud infrastructure secure. Delivering continuous, automated security, Spot Security analyzes, detects and prioritizes threats to surface the most critical vulnerabilities and provides actionable compliance, remediation and prevention.
Spot has always built products to help DevOps engineers simplify and automate the day-to-day cloud operations that they are responsible for. From cost-aware infrastructure scaling with Elastigroup, to our Ocean suite of container solutions, Spot is focused on delivering products that enable our customers to operate reliable, affordable, and scalable infrastructure in the cloud. The acquisition of cloud security specialist CloudHawk.io has enabled Spot to deliver Spot Security, allowing you to control, automate and optimize all fundamental aspects of CloudOps, all in one Spot.
The reality of security in the cloud
In the shared responsibility model of cloud security, it’s up to cloud customers to configure, manage and enforce the necessary security measures that protect their cloud environments, the applications that run in them and the data that is being held there. Security teams create and enforce policies that protect an organization, while DevOps teams implement these policies in cloud environments, enabling engineering teams to move fast and with confidence. Despite these clear responsibilities, there can be friction between these teams when it comes to decisions between policy and speed.
As part of these security protocols and processes, events that occur within a cloud environment need to be monitored and reviewed for potential threats or vulnerabilities. However, the average business produces millions of events every day, creating noise that can bury critical security threats under false alerts and low-impact issues. Without a security tool that can adapt to the ever-changing dynamic of the cloud, DevOps and security teams are left to wade through a massive amount of data to identify and understand actual security risk and potential impact. According to Google’s State of DevOps report, DevOps and security teams are wasting up to 50% of their time chasing down false positives or attending to alerts that don’t actually fix underlying problems.
Cloud infrastructure security with Spot
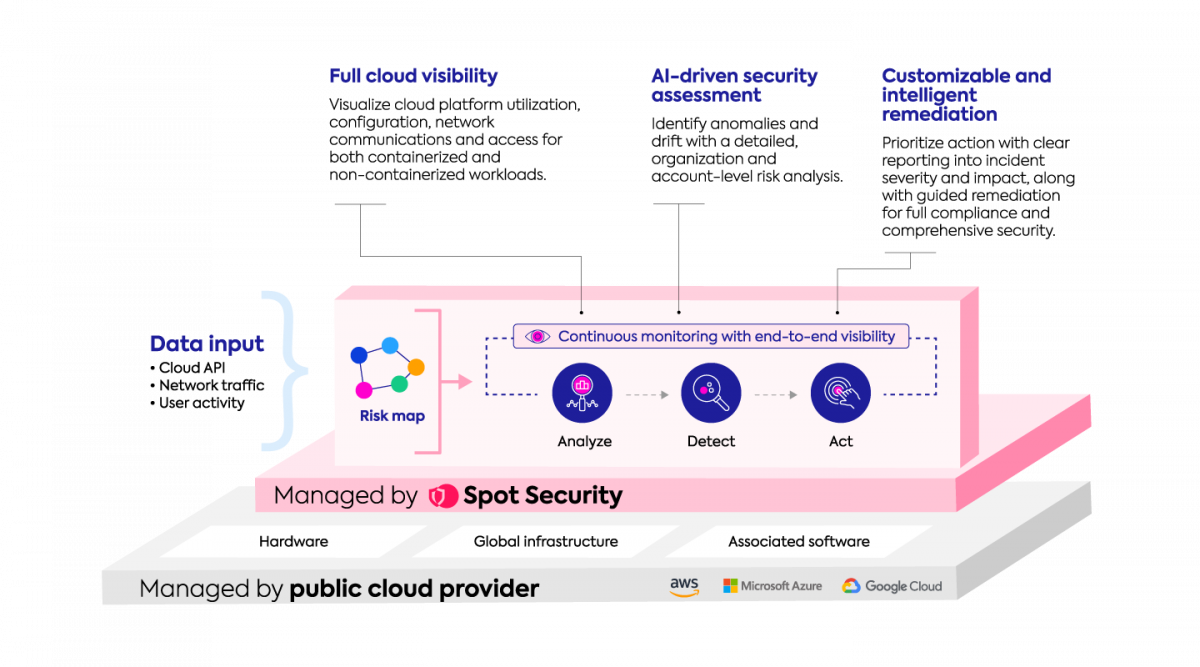
Built for the cloud, Spot Security is uniquely designed to cut through the noise, eliminate alert fatigue and remove friction between security and DevOps teams. Spot Security automates security policies and gives complete visibility into cloud infrastructure through the lens of resource relationships. By monitoring and analyzing the impact that changing cloud resources have on the whole environment, Spot Security can quickly detect, prioritize and help to mitigate the most serious security threats and risks within cloud infrastructure. With Spot Security, customers benefit from:
- 360 degree visibility into cloud environments with dashboards for security posture and attack surface, networking, asset inventories, and cloud user behaviour
- Prioritized, in-depth analytics to identify new risks, abnormal behavior and misconfigurations
- Reporting and remediation of anomalies and misconfigurations across multi-cloud infrastructure
- Support for compliance to meet industry security standards and regulatory mandates
How does Spot Security work?
The sprawling, interconnected nature of cloud environments makes it difficult for traditional security tools to piece together threats that pose the highest risks and need immediate attention. DevOps and security teams get bogged down in alerts without understanding which has the greatest potential attack surface and impact.
Spot Security, however, focuses on the relationships between dynamic cloud resources to understand the scope and breadth that a compromised resource may have on the overall account. The platform ingests data from cloud APIs, network traffic, and user activity to monitor cloud infrastructure events like access, utilization, and configuration changes.
Taking this information, Spot Security will analyze, detect and visualize the impact one resource will have on others. Every finding is assigned a score, with high scoring alerts prioritized for review and remediation. This continuous monitoring and analysis provides clear objectives, removes false positives and steers DevOps efforts to real issues.
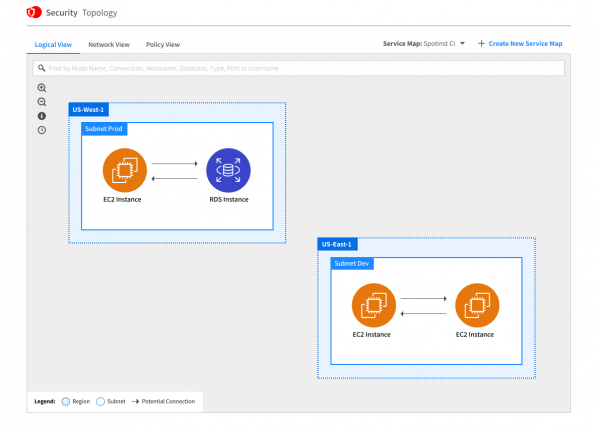
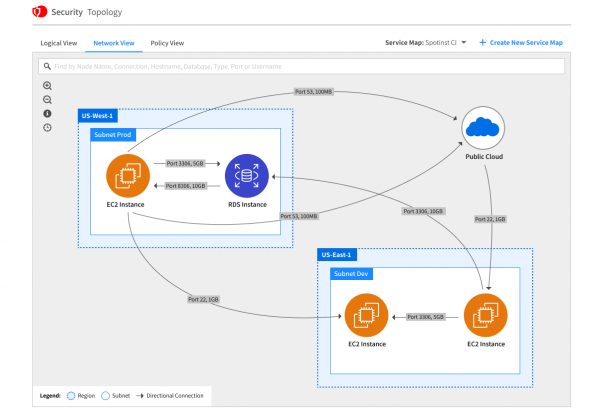
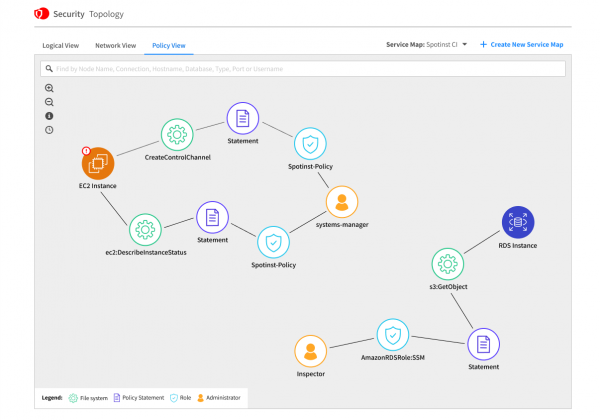
With priorities in order, users can take actions to remediate without unknowingly impacting other resources. Spot Security contextualizes resource relationships in three different views–logical, network and policy–to avoid unintended side effects that are often hard to predict.
These service maps will be accessible in the Spot Security console, and provide the underlying logic for every decision it makes. Remediations can be carried out with confidence, and applied automatically or integrated into any CI/CD pipeline.
Getting started with Spot Security
Spot Security will be available for private preview soon, to be followed by general availability on AWS and Azure. Spot Security supports EC2, S3, IAM, RDS, VPCs and other commonly used services, with more to come.
To learn more about Spot Security, visit our product page.